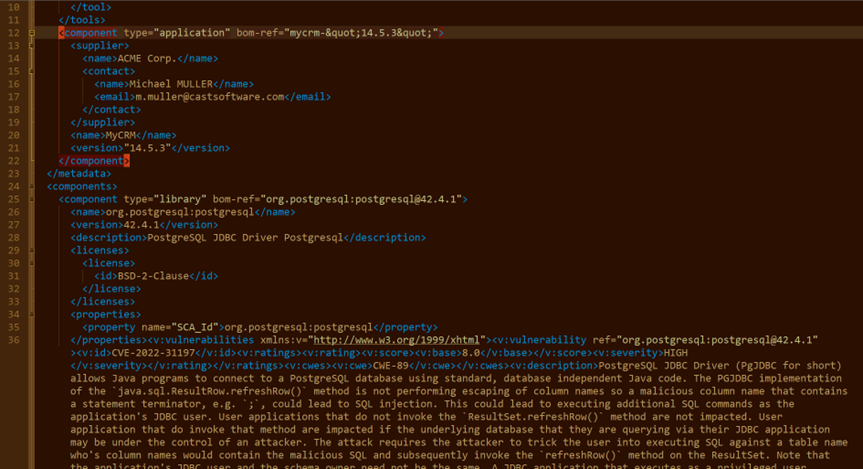
That’s why a Software Bill of Materials (SBOM) is so important and why SBOM formats like CycloneDX are emerging as standards for sharing SBOMs between, for instance, a company and its software suppliers. An SBOM is like a cooking recipe listing ingredients (software components), telling you exactly what’s inside the package. But reviewing these SBOMs manually can be a real headache. Trying to centralize and keep control of this information is even more complex at the portfolio level.
How to import a CycloneDX SBOM in CAST Highlight
If you’re familiar with CAST Highlight, you know that an application result is made of scan results and/or survey results for a given application snapshot. As an SBOM is neither a scan nor a survey, the first step will consist of creating an “empty” application result (a new snapshot if you will) which will be the placeholder for the SBOM import.
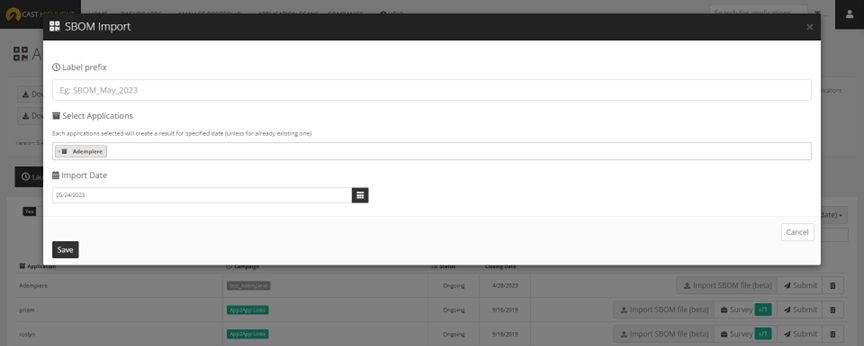
- A modal opens where you can define the snapshot label for the result you’re creating, select the applications and choose the import date.
- Once you click on ‘Save’, a new result is created for the corresponding applications with the defined closing date. You can now start the SBOM file import by clicking on ‘Import SBOM file’.
- A modal opens to upload the SBOM file (the currently supported format is CycloneDX 1.4), define a reference name for this uploaded document (by default, the reference will be the file name) and a generate date (by default, it will be current date). Note that the same SBOM file cannot be imported more than once for the same application, although the same SBOM file can be uploaded for different applications.
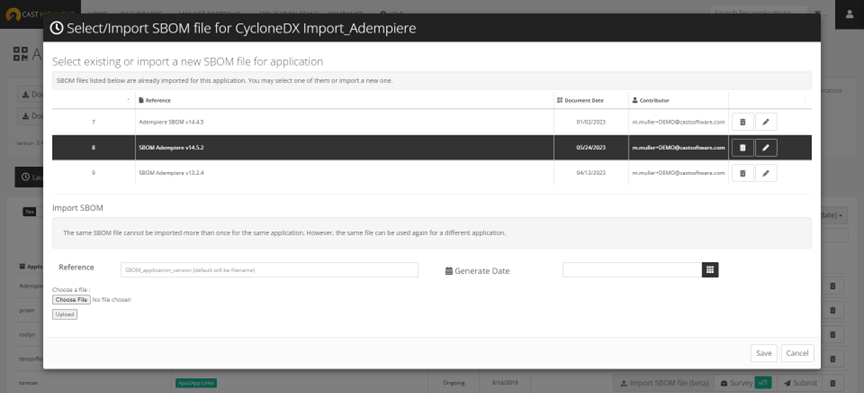
- Select the SBOM corresponding to the application snapshot and click on ‘Save’.
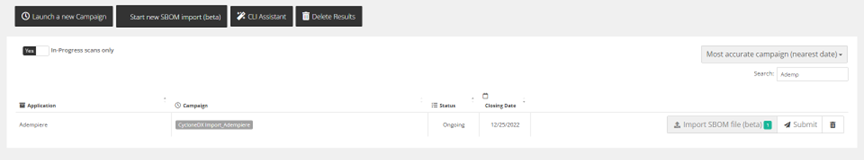
- Finally click on ‘Submit’ to run the SCA result processing for this SBOM import.
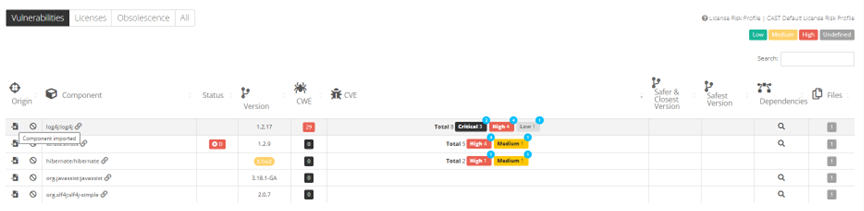
Once the SBOM import has been processed by CAST Highlight, application results are available under the Software Composition tab for the given application, exactly as if it were scanned directly. Vulnerabilities, license issues, obsolescence, list of detected components and versions, and other SCA features are available.
You will notice that the ‘Origin’ icon is slightly different from a regular scan as components are not detected through a dependency file (pom.xml, package.json, etc.) nor a scan fingerprint, but through a SBOM file import.







SHARE